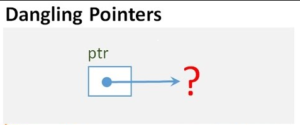
Dangling pointers and wild pointers in computer programming are pointers that do not point to a valid object of the appropriate type. These are special cases of memory safety violations
Pointer variables hold memory addresses.
Because of this, a pointer can be used to wander into a machine’s memory space.
This ability is often hailed as pointers’ greatest advantage and disadvantage.
- Good because of speed and flexibility
- Bad because f out-of-bounds memory accesses
A dangling pointer is a pointer value used by a program that points to memory that was previously valid but has since been freed. Any access through a dangling pointer is a serious memory bug. Returning addresses of stack-allocated variables from functions is guaranteed to cause dangling /wandering pointers because the stack-allocated variable is freed as the function returns.
Anyone who has worked in C suffers from pointer-wielding scars. On one hand pointers helped make C the embedded language of choice. They give us much of the power of assembly, while packaging the capabilities inside a HLL. On the other hand pointers almost always lead to travail. Novices misuse them, mixing up referencing and dereferencing, adding not enough or too many asterisk-prefixes. Professionals bypass such simple errors, but still create code that overruns buffers or writes over the code itself.
#include
int main()
{
int *p;
p=(int*)malloc(4);
*p=10;
Printf(“%dn” , *p);
free(p); //p points to destroyed memory, hence it is Dangling pointer
return 0;
}
#include
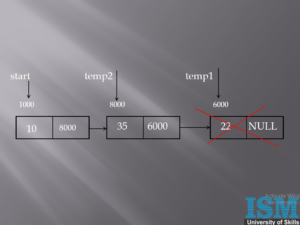
In the above picture, temp2 is a dangling pointer.
Here, temp2 holds 6000, which is the address of the destroyed memory. Hence temp2 is a dangling pointer.
Anyone who has worked in C suffers from pointer-wielding scars. On one hand pointers helped make C the embedded language of choice. They give us much of the power of assembly, while packaging the capabilities inside a HLL. On the other hand pointers almost always lead to travail. Novices misuse them, mixing up referencing and dereferencing, adding not enough or too many asterisk-prefixes. Professionals bypass such simple errors, but still create code that overruns buffers or writes over the code itself.
C compilers should come with a warning label: “Danger! Use of this product may lead to memory leaks, corrupt data, and erratic crashes.” C brings joys and perils; we must deal with both.
Though pointers create agony in pretty much every system ever produced, most of us react to each problem with surprise. Given that pointer issues are so common, why don’t we build our systems from the outset in a way to trap these inevitable problems? Why don’t we buy tools that track and flag these problems automatically?
A couple of companies do sell pointer and memory checking tools, though are mostly aimed at the desktop applications market
VALGRIND : Valgrind is a powerful memory checking tool. It is simple to use. Simply compile your program with debugging symbols, then run ‘valgrind program’. You will see extra debugging information that Valgrind provides, warning you about various types of memory issues such as uninitialized memory access, illegal reads and writes to memory and possible memory leaks.
GBD : GDB is the Linux command debugger. Similarly to Valgrind, we can invoke it on a version of our program the ‘-g’ option.
Author: Prithvi. [MBA in Digital marketing and Ecommerce]
#Embedded Courses in Bangalore #Embedded Courses in Hyderabad #Embedded Jobs for Freshers #Embedded C #Embedded Systems #Embedded Training in Hyderabad #Embedded Classes in Hyderabismuniv.com/full-stack-python-developmentad #Embedded Systems Course in Hyderabad #Embedded Programming Courses in Hyderabad #Embedded Training in Bangalore #Embedded Classes in Bangalore #Embedded Systems Course in Bangalore #Embedded Programming Courses in Bangalore #Best Embedded Training Institute in Bangalore #Best Embedded Training Institute in Hyderabad #Embedded Training Institute in Bangalore #Embedded Training Institute in Hyderabad #Best Embedded Course in Bangalore #Best Embedded Course in Hyderabad #best iot training institute in Bangalore #best iot training institute in Hyderabad #iot training institute in bangalore #iot training institute in Hyderabad #best iot course in Bangalore #best iot course in hyderabad #Embedded Jobs in Bangalore #Embedded Jobs in Hyderabad #Iot jobs in Bangalore #IoT jobs in Hyderabad #Python Jobs in Bangalore #Python Jobs in Hyderabad #AIML #Artificial Intelligence #machine learning #Data Science Courses in Bangalore #Data Science Courses in Hyderabad #Data Science Courses #Best Data Science Training Institute #Best Data science Course #Best Python Course #Best Iot Course #Best Iot Training Institute in Bangalore #Best Iot Training Institute in Hyderabad #Iot Certification Course Bangalore #Iot Certification Course Hyderabad #Best Artificial Intelligence Training Institute Bangalore #Best Artificial Intelligence Training Institute Hyderabad #Best fullstack Training Institute in Bangalore #Best full stack Training Institute in Hyderabad #full stack Training Institute in Bangalore #full stack Training Institute in Hyderabad #Best full stack Course in Bangalore #Best full stack Course in Hyderabad
useful links
www.ismuniv.com https://ismuniv.com/best-embedded-systems-and-iot-training-institute/ https://ismuniv.com/master-in-iot-development/ https://ismuniv.com/ism-univ-excellent-placements-100/ https://ismuniv.com/master-in-data-science-with-ai-ml/ https://ismuniv.com/master-in-ai-ml-programming/ https://ismuniv.com/full-stack-python-development/ https://ismuniv.com/full-stack-java-development/


